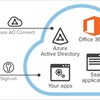
Securing non-human identities is just as critical as managing human ones in today's complex IT landscapes. Non-human identities, such as service accounts, application identities, and IoT devices, play pivotal roles in automation and system integration…
- Products
- Solutions
- Resources
- Trials
- Support
- Partners
- Communities